Exploit.education binary exploitation exercise typically runs on ASLR (Address space layout randomization) disabled ubuntu based virtual machine with Data Execution Prevention turned off binaries. In order to setup the exploit.education lab, You’ll have to either use virtualbox or qemu based virtual machine emulator setup to easily test and debug the exercises.
Installation
For both MacOS and Windows, grab a copy of qemu emulator and follow the installation setup which is quite easy.
Virtual Machine Setup
Grab a copy of Phoenix Qemu Image based on your system arch (most probably amd64) and follow the instruction below,
MacOS Setup
tar xJf exploit-education-phoenix-amd64-v1.0.0-alpha-3.tar.xzcd exploit-education-phoenix-amd64/./boot-exploit-education-phoenix-amd64.sh(after chmod u+x)
Windows Setup
- On Windows, you could unzip using
winzipor7z cd exploit-education-phoenix-amd64/- Right click on
boot.ps1>Run with Powershell
(or)
- execute on Command Prompt
> qemu-system-x86_64.exe -kernel vmlinuz-4.9.0-8-amd64 -initrd initrd.img-4.9.0-8-amd64 -append "root=/dev/vda1" -m 2048M -netdev user,id=unet,hostfwd=tcp:127.0.0.1:2222-:22 -device virtio-net,netdev=unet -drive file=exploit-education-phoenix-amd64.qcow2,if=virtio,format=qcow2,index=0
SSH Setup
You can use your favourite ssh applications such as PuTTY or plain terminal would do this job,
ssh -p2222 user@localhost
As published on exploit.education website, password for user:user and root:root
Playground
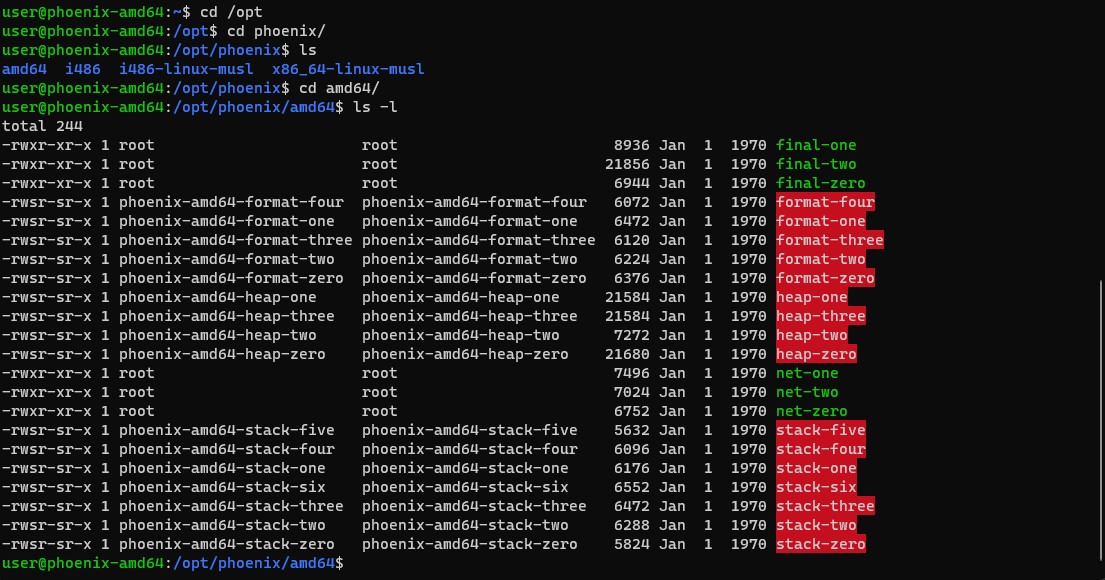
You can headover to /opt/phoenix/amd64 to start playing around the with the binaries 🎉
Source and Reference:
Closing Note:
I hope this post is helpful for vulnerability researcher 🔍 & code reviewers, For bugs,hugs & discussion, DM in Twitter. Opinions are my own and not the views of my employer.